Setting up Windows Defender Advanced Threat Protection

Understanding what Windows Defender Advanced Threat Protection (ATP) actually is had eluded me for a while - it’s not included in something like EMS, it’s not available with a Visual Studio Enterprise subscription and you’ll need to request an evaluation from Microsoft (and hope it’s approved) to test it out. Windows Defender ATP is licensed as a component of the Windows 10 Enterprise E5 or the Secure Productive Enterprise (soon to be Microsoft 365) E5 subscriptions.
So what is ATP? According to Microsoft, Windows Defender Advanced Threat Protection is:
Windows Defender Advanced Threat Protection (Windows Defender ATP) is a security service that enables enterprise customers to detect, investigate, and respond to advanced threats on their networks.
…
Windows Defender ATP uses the following combination of technology built into Windows 10 and Microsoft’s robust cloud service:
Endpoint behavioral sensors:
- Embedded in Windows 10, these sensors collect and process behavioral signals from the operating system (for example, process, registry, file, and network communications) and sends this sensor data to your private, isolated, cloud instance of Windows Defender ATP.
- Cloud security analytics: Leveraging big-data, machine-learning, and unique Microsoft optics across the Windows ecosystem (such as the Microsoft Malicious Software Removal Tool, enterprise cloud products (such as Office 365), and online assets (such as Bing and SmartScreen URL reputation), behavioral signals are translated into insights, detections, and recommended responses to advanced threats.
- Threat intelligence: Generated by Microsoft hunters, security teams, and augmented by threat intelligence provided by partners, threat intelligence enables Windows Defender ATP to identify attacker tools, techniques, and procedures, and generate alerts when these are observed in collected sensor data.
In short, Windows Defender ATP is a cloud-based threat management/protection solution for Windows 10 that does not require deployment of agents (because they’re inbox features), that will also work with 3rd party anti-virus solutions.
Microsoft positions ATP for enterprise customers, but given the integration with their other products and that it’s a completely cloud-hosted platform, this should be for everyone (budget concerns aside). Many small to medium organisations (and partners) that I talk to are actively looking at ways to reduce their on-premises infrastructure.
Setting up Windows Defender Advanced Threat Protection
To give you an idea of what does the setup process for ATP looks like, I’ve documented the experience during setup in my own tenant. The gallery below shows a screenshot of each step including onboarding a device and performing a detection test.
Windows Defender ATP setup welcome page
Step 1: Selecting the Windows Defender Advanced Threat Protection data storage location
Step 2: Select a data retention policy
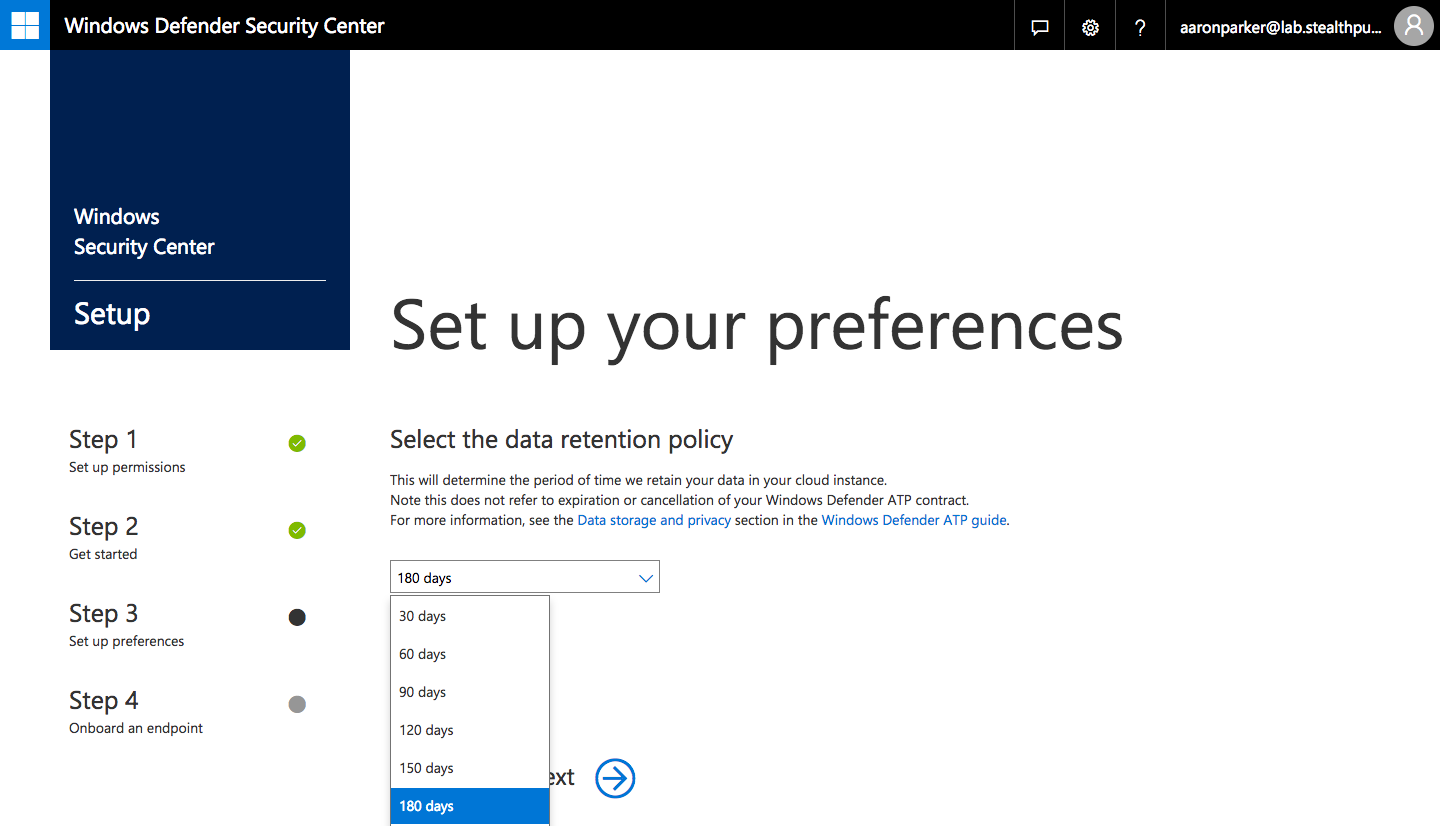
Step 3: Data retention up to 180 days is possible
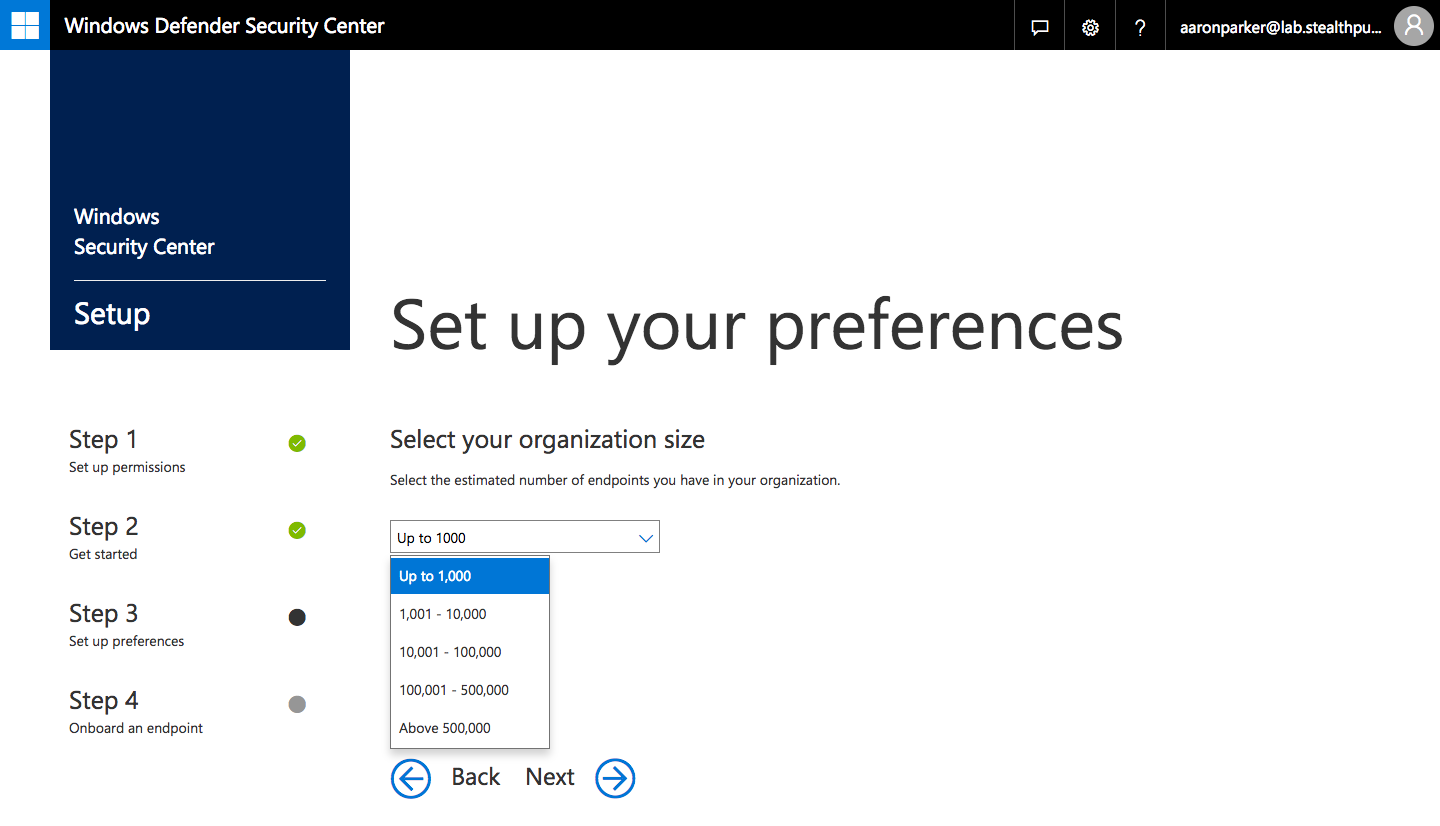
Step 4: Select your organisation size
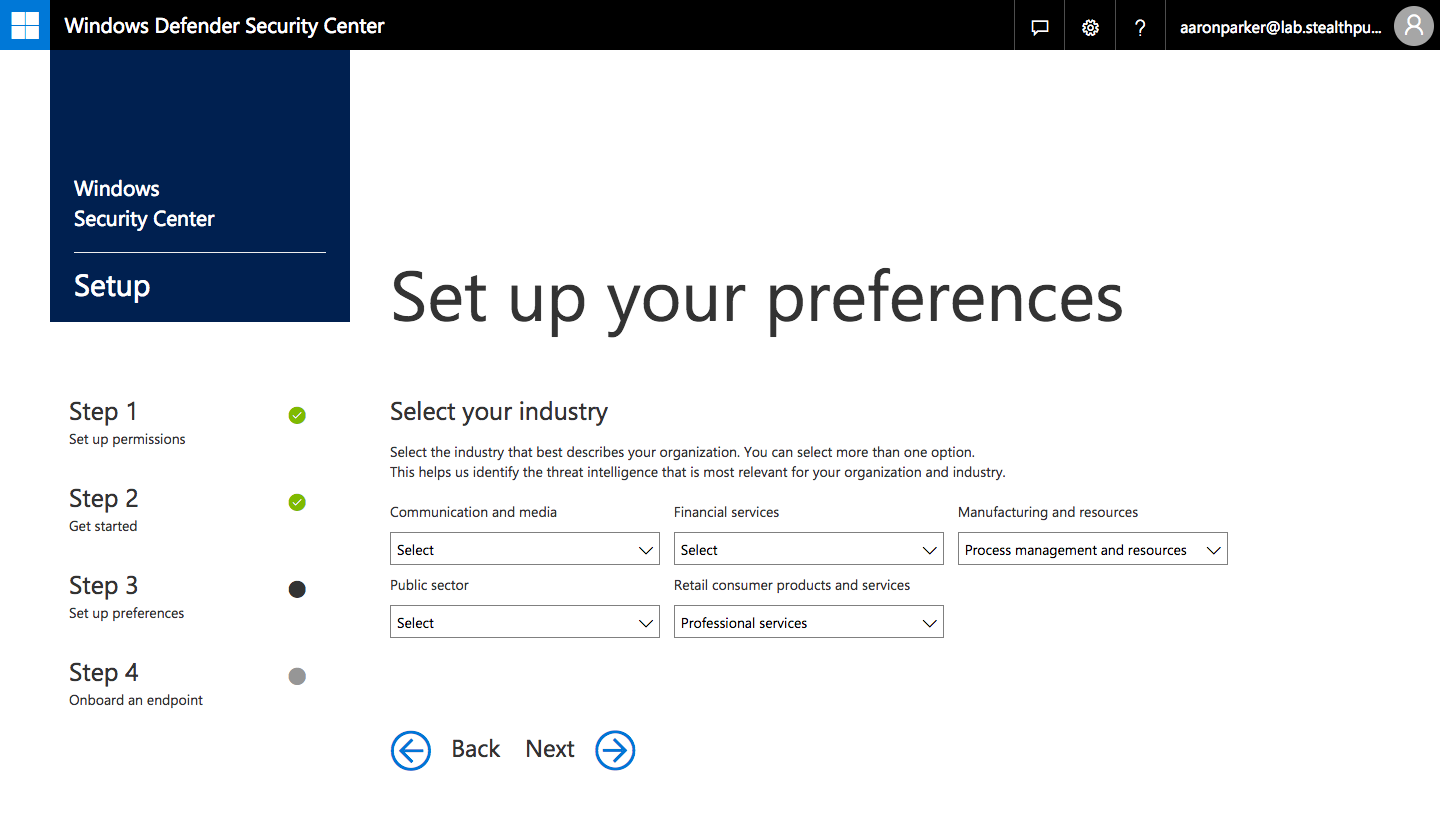
Step 5: Select your industry from a limited selection
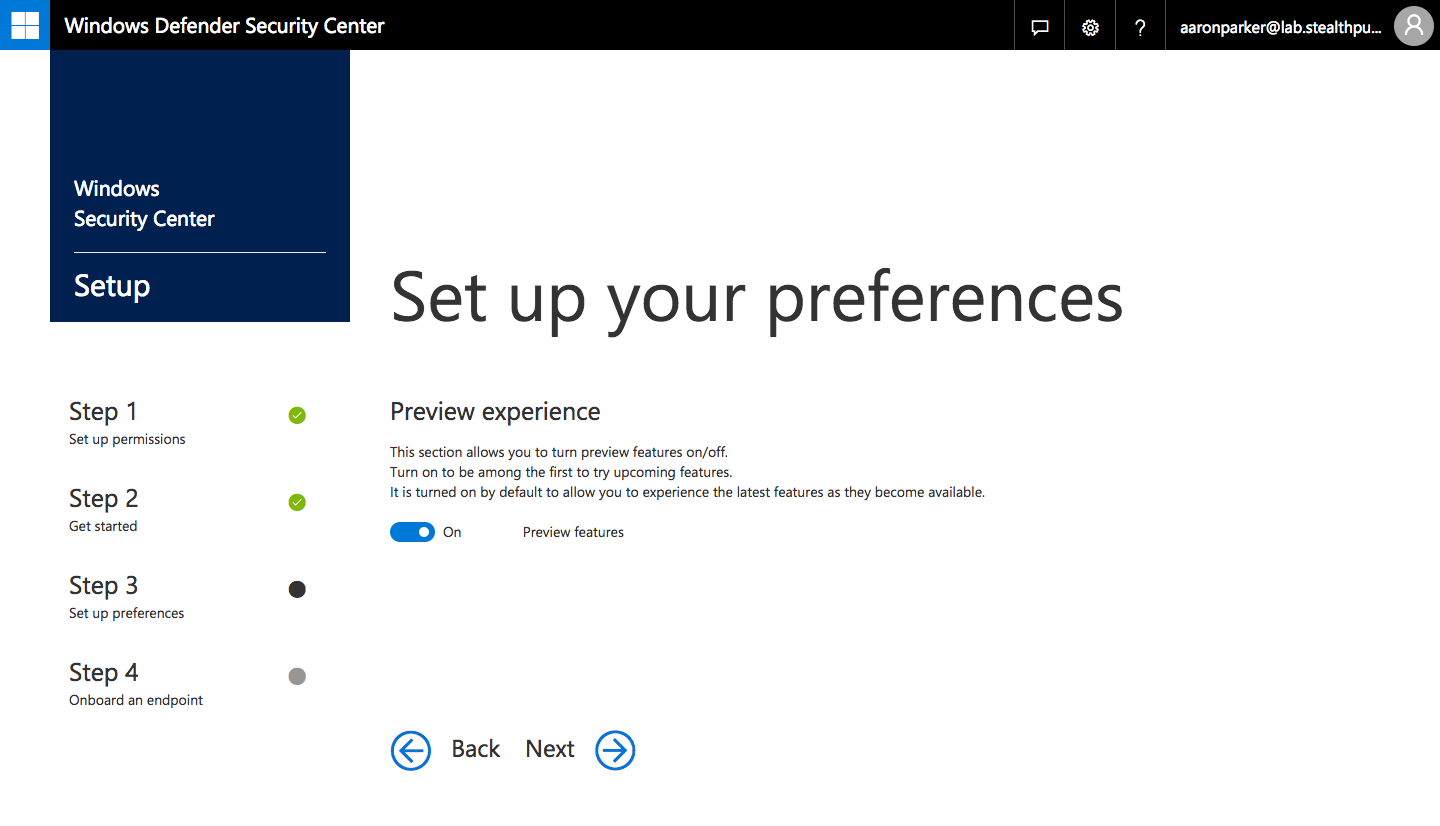
Step 6: Choose to enable preview features
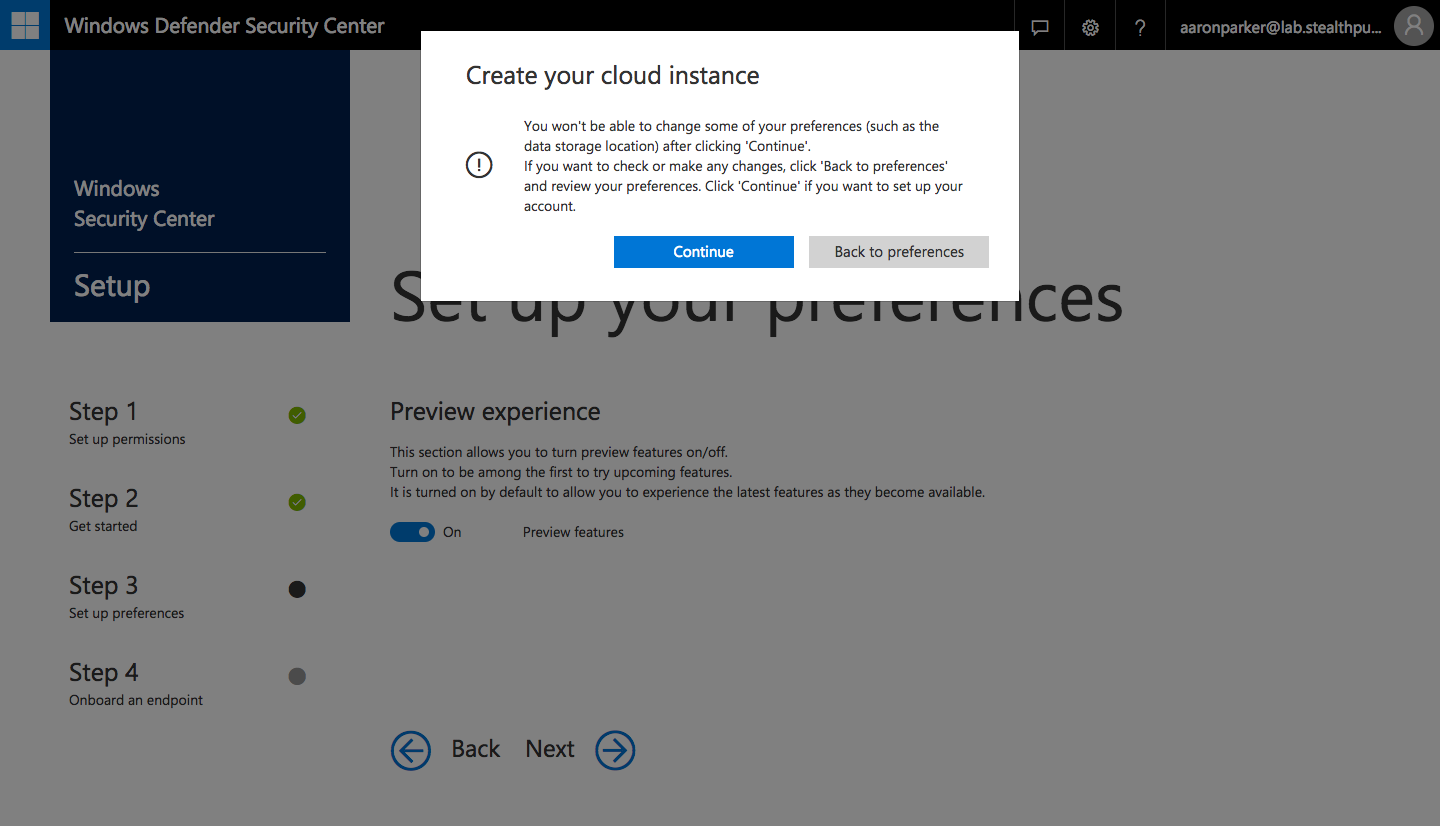
Step 7: Confirm creation of your Windows Defender ATP cloud instance
Progress seen when creating the cloud instance
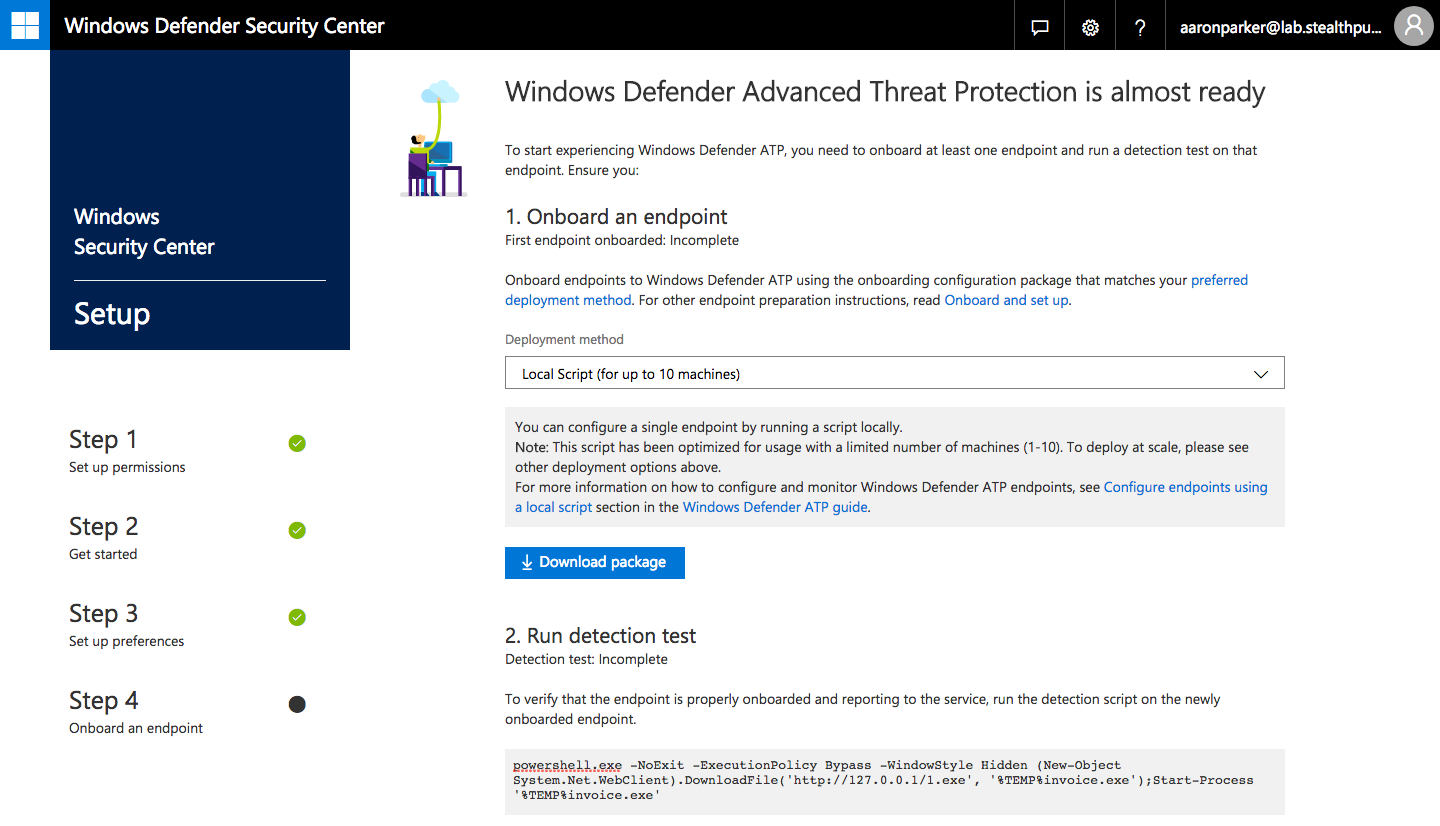
Step 8: Onboard and end-point and test detection
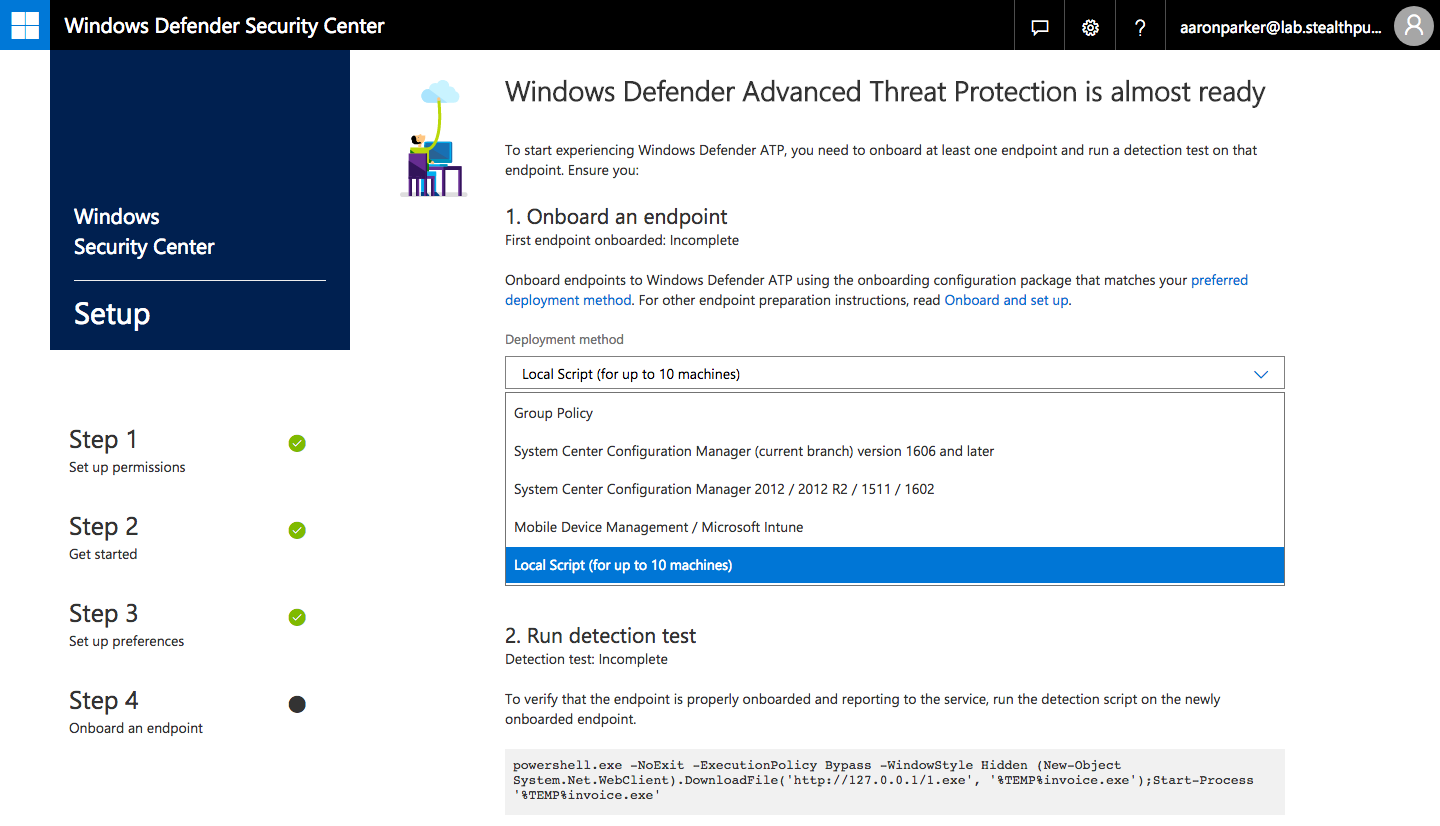
Onboarding deployment methods
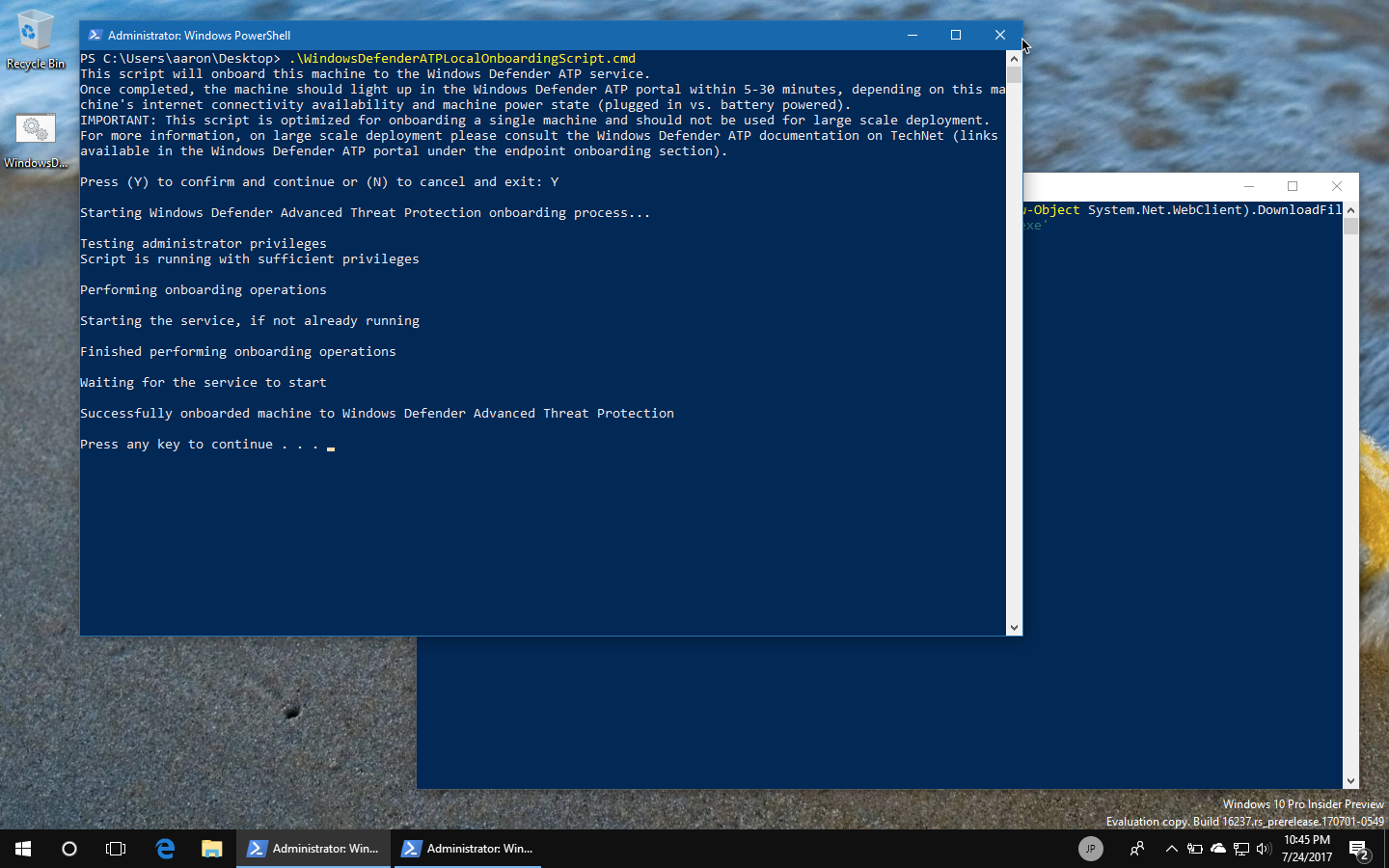
Step 9: Onboarding a Windows 10 device with a script
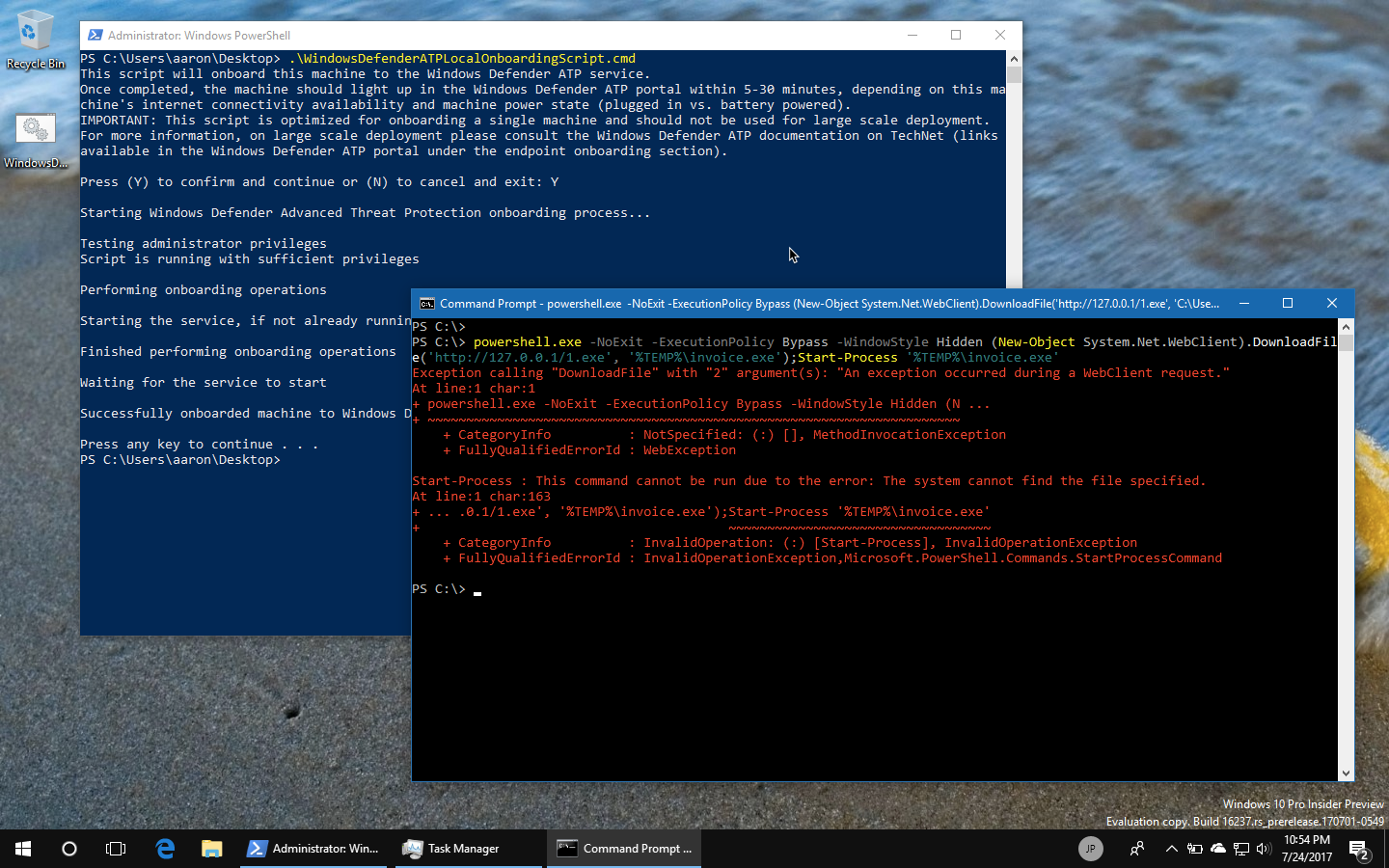
Step 10: Running the detection test
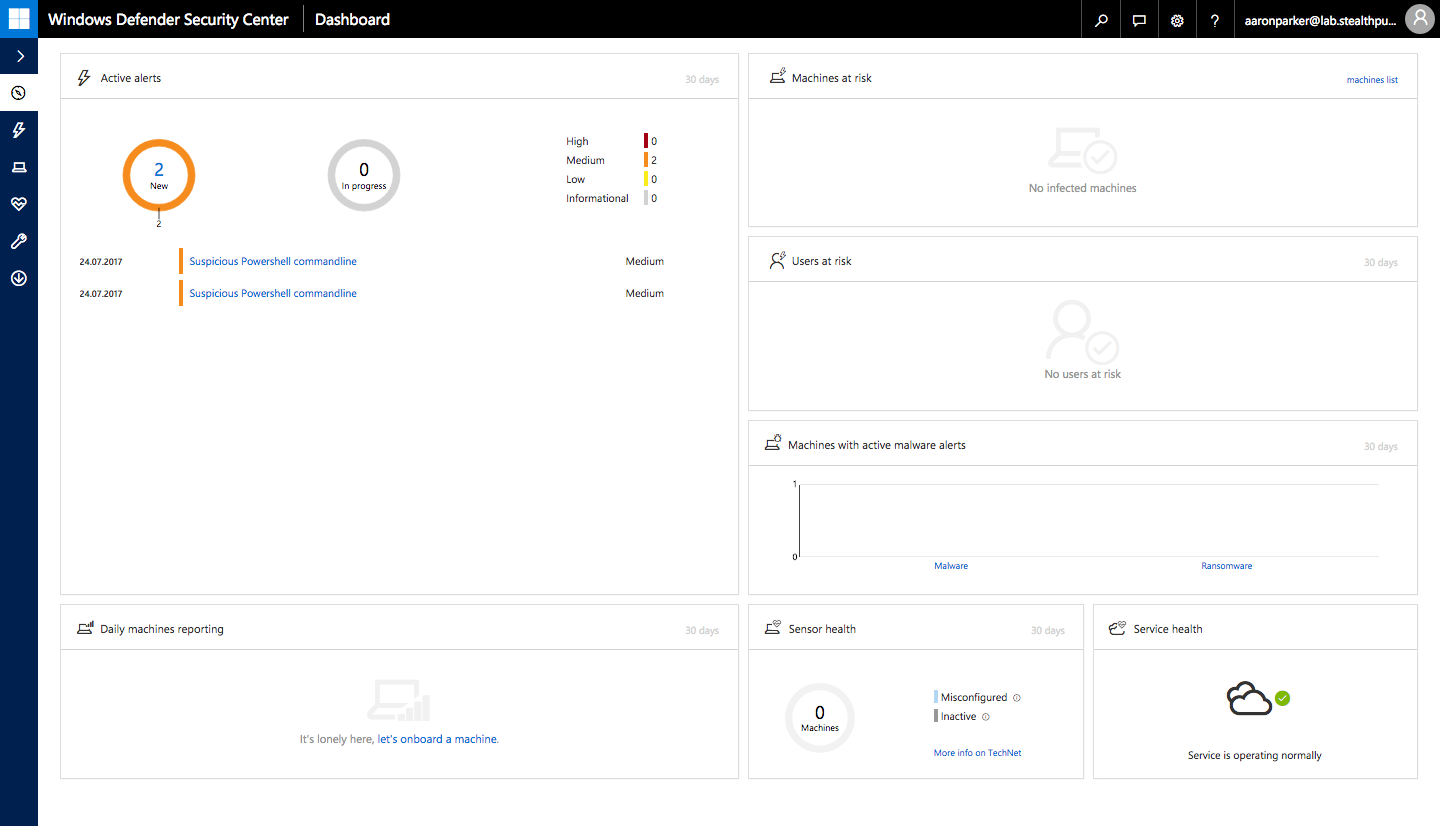
The Windows Defender ATP Dashboard
Provisioning ATP is as easy process - the hardest part for me was working out where to access to the console - if you’re looking for it, here it is: https://securitycenter.windows.com/
Onboard a Windows 10 device with Intune
With ATP deployed, you can now use Intune (or another MDM solution) to onboard a device into ATP. You could also use Group Policy, ConfigMgr, or a script.
Previously you would have to need to create a custom Intune policy to push out an OMA-URI setting. Now in the Azure portal, pushing out the policy is easier. Intune provides an in-built profile for onboarding and offboarding devices using configuration packages downloaded from the ATP console.
Create a new profile for Windows 10, choose the ‘Windows Defender ATP (Windows 10 Desktop)’ profile type and select the onboarding package. In the screenshot below, I have populated both the onboarding and offboarding packages, but you would only deploy an onboarding package.
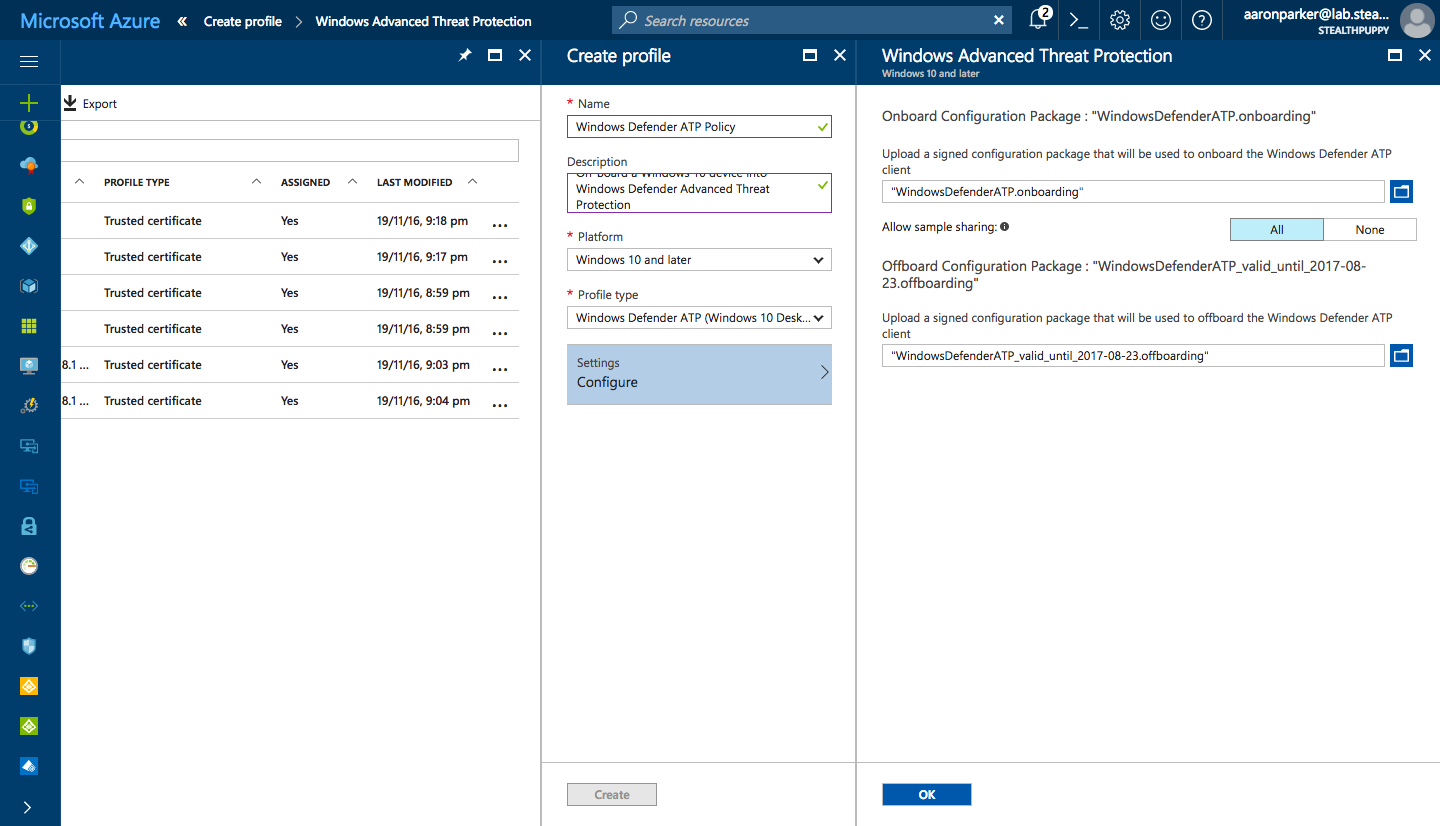
Configure the Windows ATP onboard and offboard package in Microsoft Intune
With the profile created, assign it to a group. In my example here, I’m assigning the profile to a Windows 10 dynamic group.
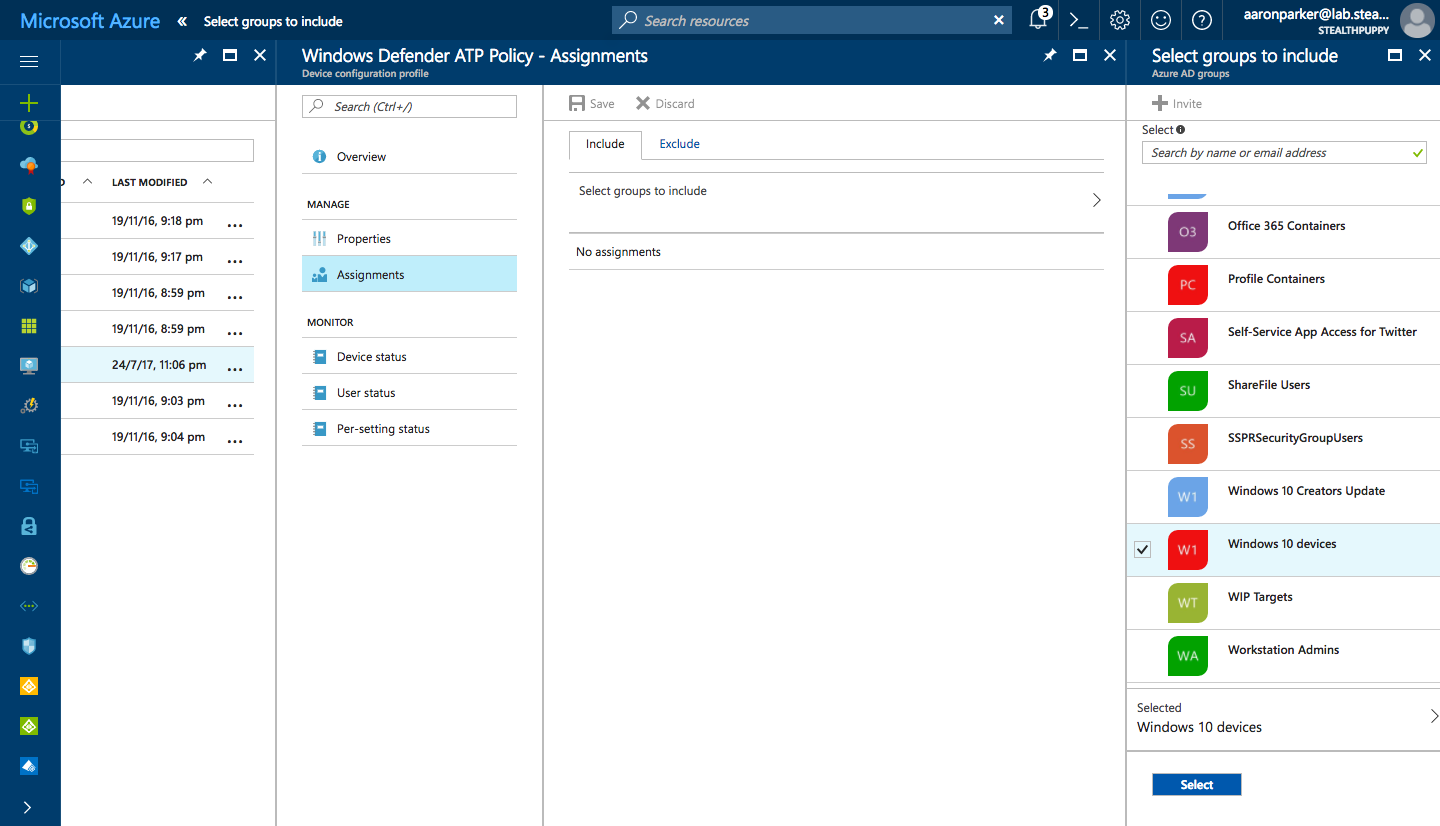
Target the Intune policy to a device (or user) group
With devices onboarded, you can start monitoring them in the Windows Defender ATP console:
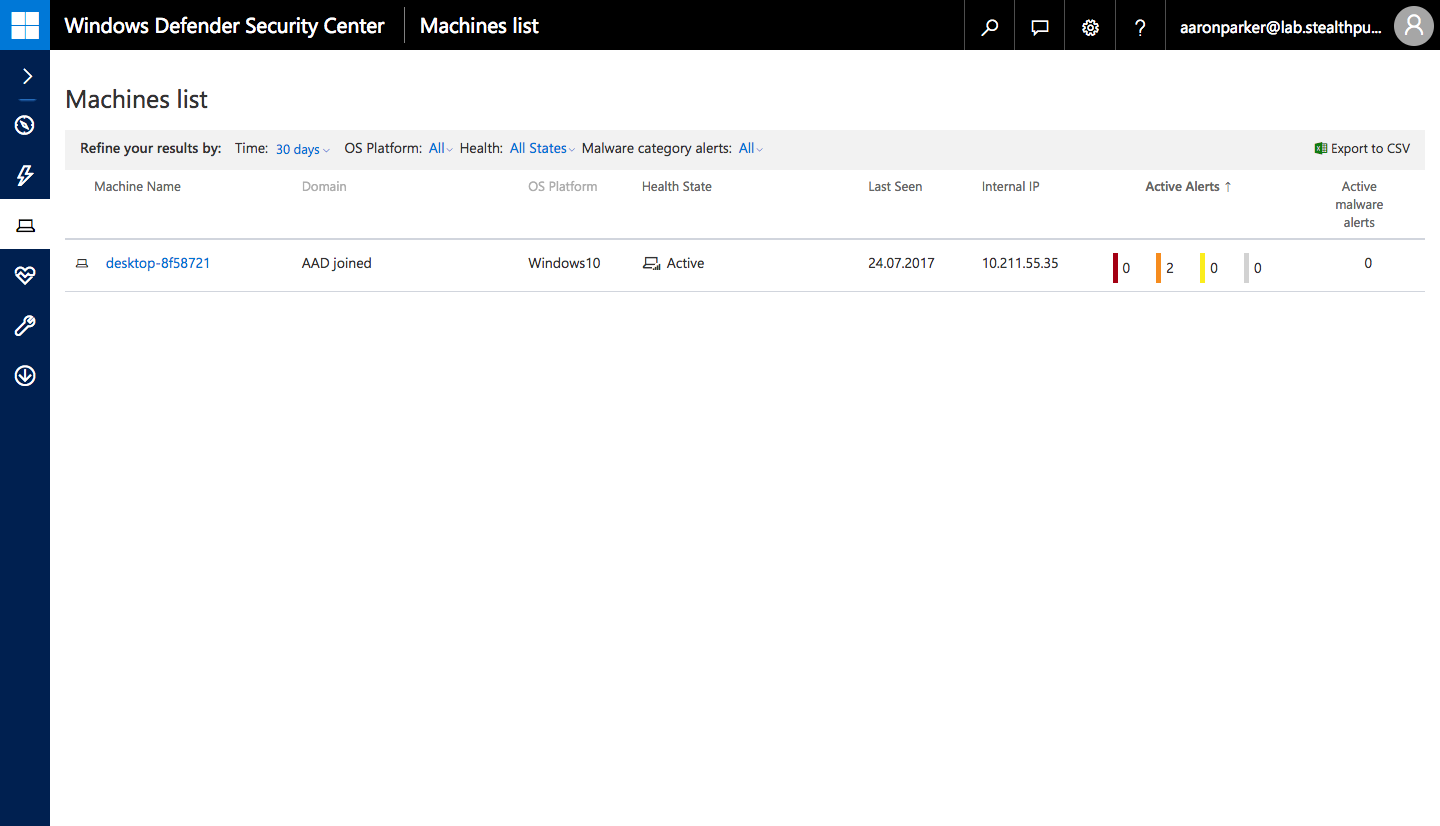
Machines List in the Windows Defender ATP console
I may dig further into Windows Defender Advanced Threat Protection features in a future article.
