Configuring Remote Desktop Certificates for OS X Clients
Windows has supported TLS for server authentication with RDP going back to Windows Server 2003 SP1. When connecting to a Windows PC, unless certificates have been configured, the remote PC presents a self-signed certificate, which results in a warning prompt from the Remote Desktop client. An environment with an enterprise certificate authority can enable certificate autoenrollment to enable trusted certificates on the RDP listener, thus removing the prompt. To get OS X clients to accept the certificate takes a little extra configuration not required on Windows clients.
While I may only be configuring certificates in my lab environment, there’s not much effort required to remove these certificate warnings.
Client Warnings for Untrusted Certificates
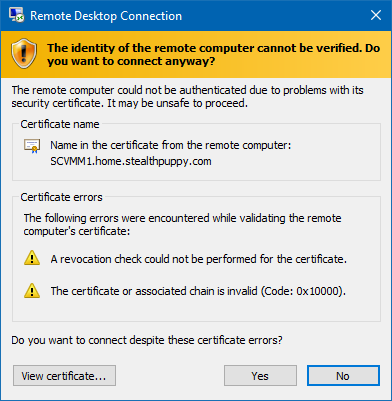
Here are the client certificate warnings on various Microsoft Remote Desktop clients, including OS X. First up the original Remote Desktop Connection (mstsc) on Windows:
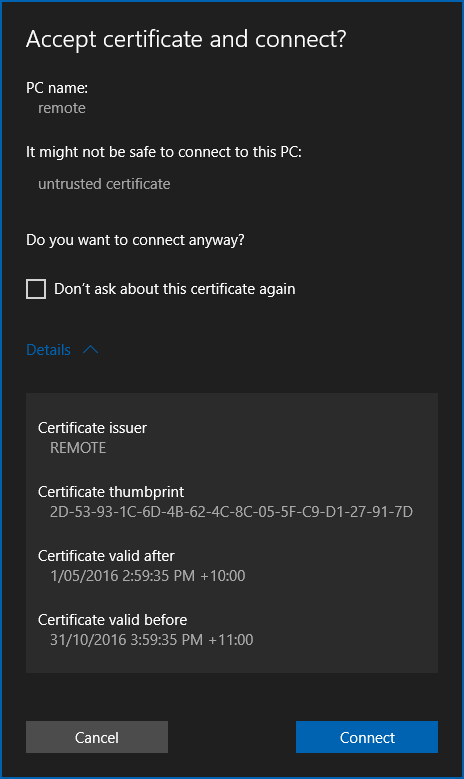
The new Remote Desktop Universal app on Windows 10:
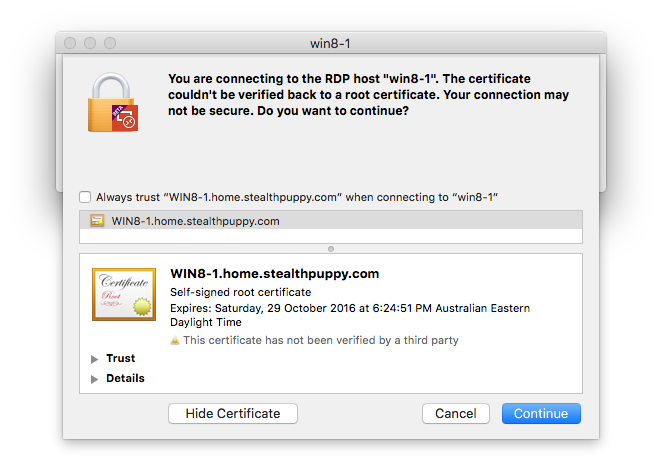
And the Remote Desktop client on OS X 10.11:
Configuring the Certificate Template
I won’t cover installing and configuring an enterprise certificate authority here; however, here are a number of articles worth reading on this topic:
- Certification Authority Guidance
- Enterprise PKI with Windows Server 2012 R2 Active Directory Certificate Services (Part 1 of 2)
- Enterprise PKI with Windows Server 2012 R2 Active Directory Certificate Services (Part 2 of 2)
- Using certificates in Remote Desktop Services
To configure a certificate for use with Remote Desktop Services (or RDP into any Windows PC), you’ll need to create a new certificate template and enable both the Server Authentication and the Remote Desktop Authentication application policies. This was key for OS X clients - both of these policies must exist. Some articles will walk through this configuration and recommend removing the Server Authentication policy; however, the certificates will then not work on non-Windows clients.
This article has a great walk-through of the entire process and more: RDP TLS Certificate Deployment Using GPO. In my lab, I’ve created a ‘Remote Desktop Computer’ certificate template and enabled it to be autoenrolled via Group Policy.
Certificate Template Options
To create the new template, open the Certificate Templates console and duplicate the Computer template. Use this template because it already has the Server Authentication policy enabled.
Navigate to the Extensions tab, edit the ‘Application Policies’ extension and remove ‘Client Authentication’ from the list.
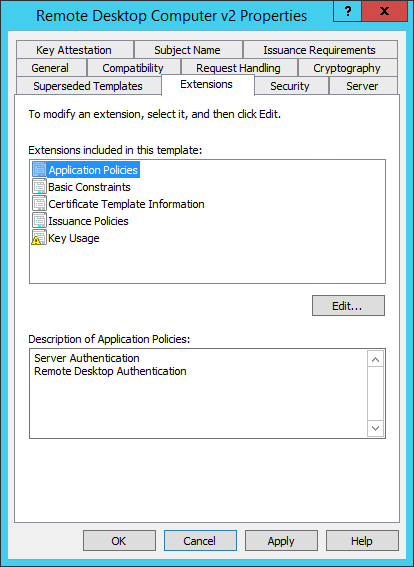
After you added the ‘Remote Desktop Authentication’ policy, you should see the policies and see in the following dialog box. See below for the actual ‘Remote Desktop Authentication’ policy.
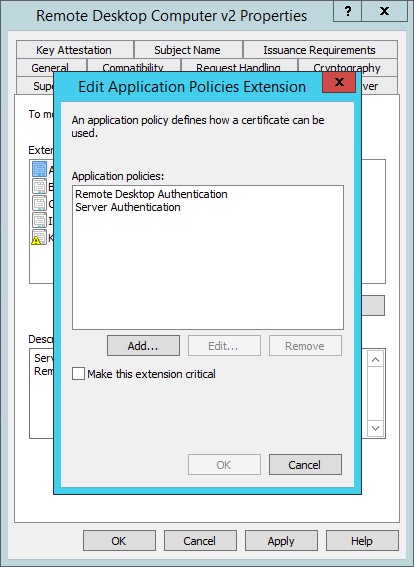
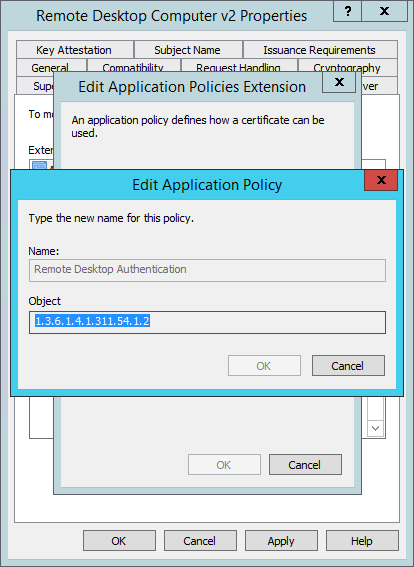
Adding the ‘Remote Desktop Authentication’ policy requires adding a new extension named ‘Remote Desktop Authentication’ (or similar) with an object value of “1.3.6.1.4.1.311.54.1.2” (excluding quotes). and enter the values as above.
Save the template and configure your CA to issue the new template. In my lab my certificate template display name ‘Remote Desktop Computer’. Since my first template failed, it’s actually called ‘Remote Desktop Computer v2’. However, the important name to note for the next step is the actual template name, which can be found on the General tab of the template. In my case this is ‘RemoteDesktopComputerv2’ (the display name, minus the spaces).
Configure Autorenrollment
To configure autoenrollment, I’ve created a new GPO dedicated to the autoenrollment setting and linked it to the organisational units containing server and workstation computer account objects. Edit the policy and enable the following setting:
Computer Configuration / Administrative Templates / Windows Components / Remote Desktop Services / Remote Desktop Session Host / Security / Server authentication certificate template
Add the name of the certificate template and shown in the screenshot below:
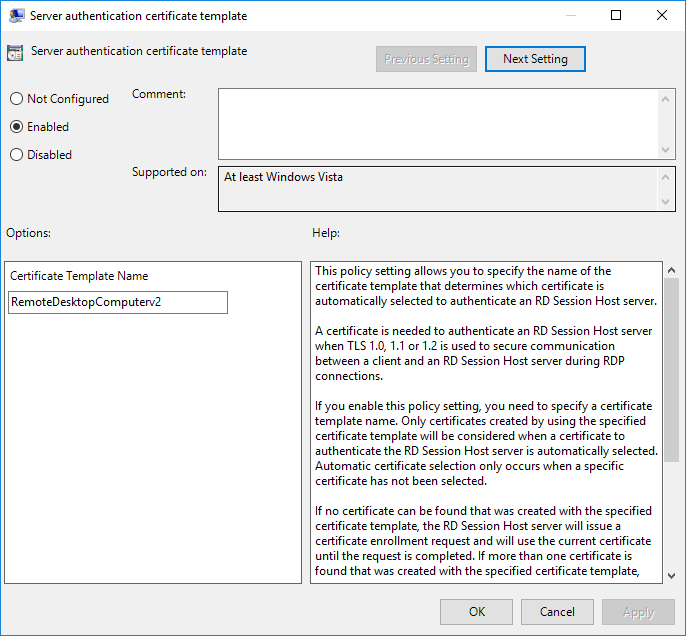
Once a Group Poliy refresh occurs or on the next boot, the target Windows machines will autoenroll for the certificate and configure their RDP listener.
OS X Configuration
Now that my Remote Desktop certificates are configured for autoentrollment and Windows machines are picking up the certificates, I can import the root CA certificate into my MacBook running OS X.
Navigate to the URL of your certificate server (e.g. http://cert1/certsrv) and download the certificate via ‘Download a CA certificate, certificate chain, or CRL’. Download the CA certificate in DER format. Find the downloaded certificate in Finder and open the certificate to install it into Keychain.
Once installed the certificate is not automatically trusted as you can see below:
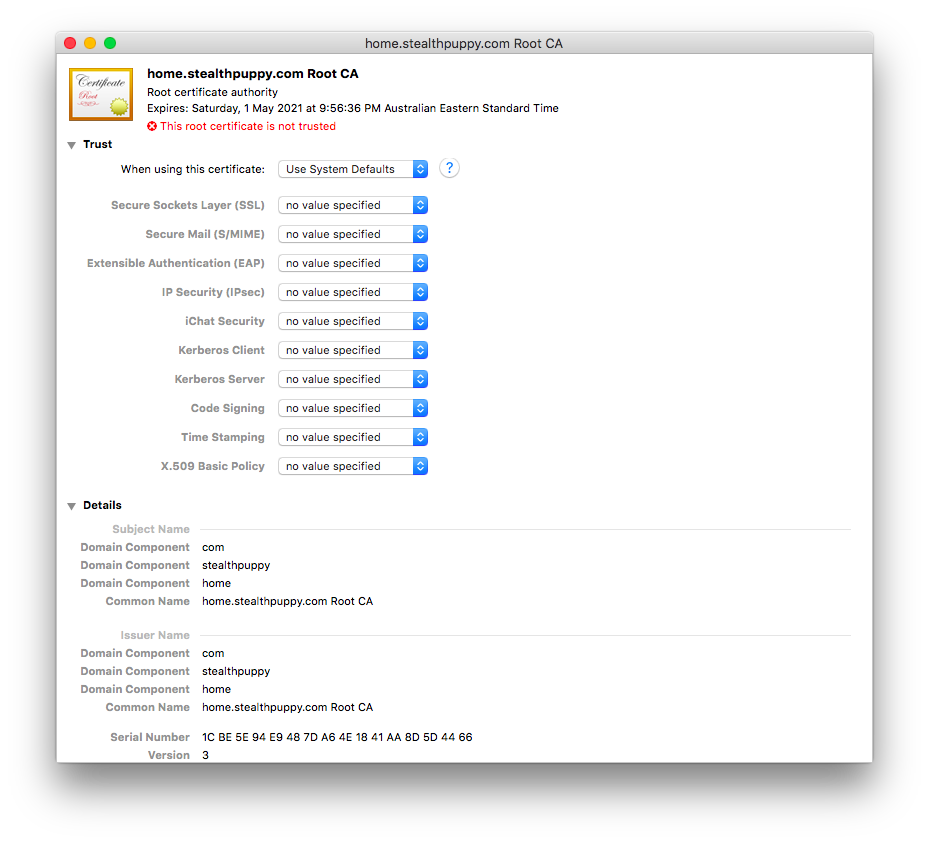
Set the certificate to be trusted by selecting ‘Alway Trust’ from the ‘When using this certificate’ option. Close the certificate properties window and you should be prompted for your password to save the changes. Now when connecting to PCs via the Remote Desktop client, you should no longer receive certificate warnings.
This article shows how to install the root CA certificate via Terminal, which should assist in automating the import across a number of Macs.
