Fixing Windows Explorer security warning prompts
Last week I wrote about avoiding Explorer’s Security Warning prompts, this time around I want to document a related fix that I’ve had to implement because Explorer’s expected behaviour was not just not working.
First a quick background on what we’re trying to solve. By default, Windows Explorer will place network locations (mapped drives and UNC paths) with a period (.) in the path, into the the Internet zone. This means that when users access files from these locations, they will see security warnings like these:
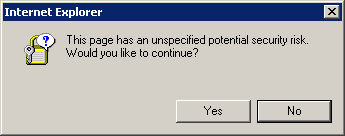
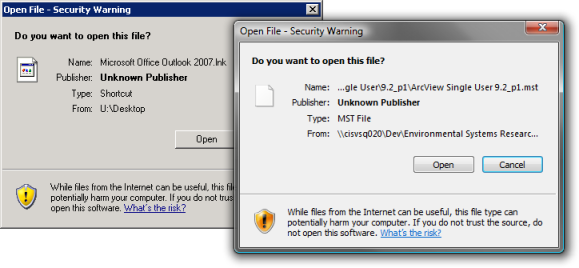
These warnings attempt to ensure users are aware of the potential risks when opening files from un-trusted locations. You can make a location trusted by adding it to the Local Intranet or Trusted Sites zones. This is exactly what you would do via script, Group Policy or some other workspace management tool, for your internal network locations, so that users do not see these prompts. However, a bug exists where drives mapped to these network locations are not placed into the right zone.
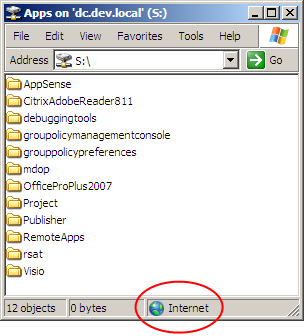
If you map a drive to a UNC path that that includes two or more periods in the name you will see that the network drive is marked as being in the Internet zone even though you may have added the location to the Local Intranet zone. In my example here, I’ve mapped drive S: to \dc.dev.local\Apps, and as you can see, it’s in the Internet zone:
If I open the same location via a UNC path you will see that Explorer sees it as being in the Local Intranet zone:
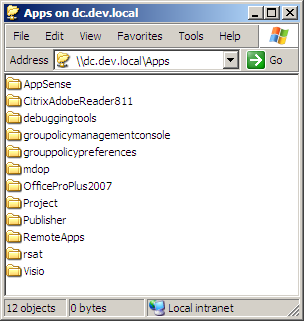
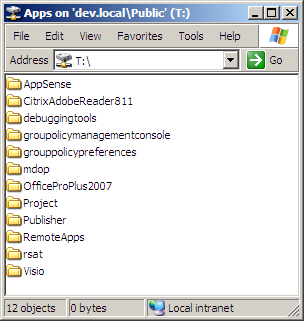
Oddly enough, if I map a network drive to a path with only a single period on that path, the detection process works correctly and the location is seen as Intranet. In the example here, I’m mapping a drive to the same location as the previous two screen shots, but via a DFS path - \\dev.local\Public\Apps that redirects to \\dc.dev.local\Apps.
This issue is addressed in the following knowledge base article:
The article details a hotfix that is available for Windows Vista and Windows XP Service Pack 2 and the issue has been addressed in Windows Vista Service Pack 1 and Windows XP Service Pack 3. For Windows Server 2003 the issue is fixed in the latest cumulative security update for Internet Explorer. To install the fix when deploying this update you need to use the QFE switch:
IE7-WindowsServer2003-KB950759-x86-ENU.exe /B:SP2QFE
To enable the fixed behaviour for each of the operating system versions, including Vista SP1 and XP SP3, you also have to add the following registry value. See the KB article for more details.
Windows Registry Editor Version 5.00
[HKEY\_LOCAL\_MACHINE\SOFTWARE\Microsoft\Internet Explorer\MAIN\FeatureControl\FEATURE\_RESPECT\_ZONEMAP\_FOR\_MAPPED\_DRIVES\_KB929798]
"*"=dword:00000001
For anyone who can’t yet deploy Windows Vista SP1 or Windows XP SP3, you may be able (I haven’t tested) to deploy the IE cumulative security update instead of the hotfix.
