Avoiding Explorer’s Security Warning Prompts
Windows XP Service Pack 2 and Windows Server 2003 Service Pack 1 made some changes to the way Windows handles specific file types opened or downloaded from certain locations, which results in Open File – Security Warning prompts like these:
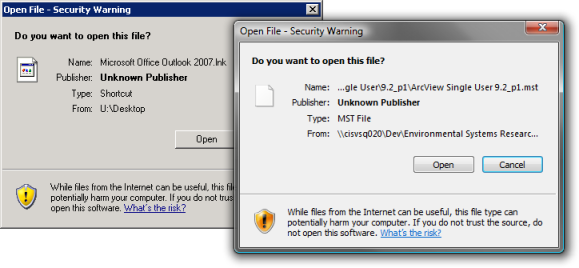
Quite often users see these prompts in environments where files are opened from UNC paths (think mapped drives or redirected folders) on Distributed File System namespaces. If you have this scenario (which I think you should be) because you are doing something like redirecting Start Menus, you can disable these prompts for your internal network locations.
Ideally you would do this by deploying specific Intranet zone settings (as in the screenshots below) or adding your internal sites to the Intranet zone via a script, Group Policy (Preferences or Internet Explorer Maintenance) or your tool of choice.
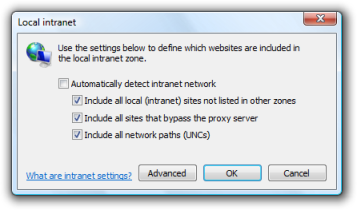
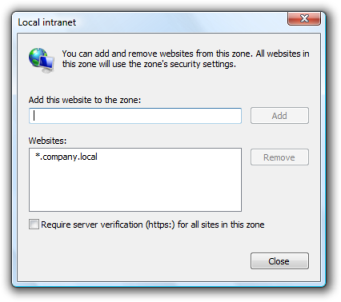
There’s a heap of information on how this stuff works at these links:
- Description of how the Attachment Manager works in Windows XP Service Pack 2.
- Configure the Attachment Manager in Windows XP SP2
- Intranet site is identified as an Internet site when you use an FQDN or an IP address
- You might even need to look into this hotfix, this hotfix or even this hotfix if things aren’t working as expected.
But all of that is not really the point of this post. I stumbled across a really simple method of telling Windows to avoid those checks and just open the files – create the environment variable SEE_MASK_NOZONECHECKS and set it to 1. You can set this as system environment variable but it appeared to be a little more consistent if set as a user environment variable. Not recommended for wide scale deployment but useful none the less.
